Archive for the 'USB' Category
Thursday, June 25th, 2009
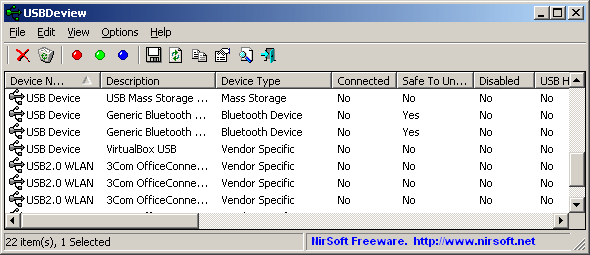 Chances are, you have at least a couple of USB devices connected to your computer at times. It’s a given nowadays to have flash drives, portable hard discs, printers,MP3 players, and other devices regularly connecting through USB ports; So chances are,you’ve likely got rather a few by now. Would you like to know how many, and be able to keep track of what they’re doing? Chances are, you have at least a couple of USB devices connected to your computer at times. It’s a given nowadays to have flash drives, portable hard discs, printers,MP3 players, and other devices regularly connecting through USB ports; So chances are,you’ve likely got rather a few by now. Would you like to know how many, and be able to keep track of what they’re doing?
USBDeview is a program for maintaining a watch over everything USB on your computer. It doesn’t just report on USB devices currently attached — device name, type of device, connection status — it also keeps a database of things previously connected too. Do you want to uninstall a device? This program can help you out. How about disconnecting something currently connected? It can help you do that too. You’ll even be able to keep track of USB devices connected to a remote machine too! assuming you’re logged-on as an Administrator.
What’s more, its freeware, so if you wanna take it for a test ride and you enjoy it, it’s yours to keep.
Visit the homepage here
Posted in Flash, Freeware, USB | 1 Comment »
Thursday, August 28th, 2008
 IdentityPal Lost & Found is a free service to help reunite lost USB pen drives with their owners. IdentityPal Lost & Found is a free service to help reunite lost USB pen drives with their owners.
No installation is necessary. Just download the ZIP file,and copy the files to the root directory of your USB drive, and thats it! When it’s inserted into a computer, it will then display a main screen containing an address of the IdentityPal Service, ready for printing out. Whoever found your USB pen drive can then return it to you for free via IdentityPal’s Postage-Paid Return Mailing Service.
This service ships a lost USB drive back to its registered owner while keeping their personal information totally private.
Once your tracking ID is confirmed,your drive will be shipped back to you at no charge. This is worth trying out if you worry about losing your USB drive and its totally free.
Check it out and download here.
Posted in Freeware, Main, USB | No Comments »
Wednesday, March 21st, 2007
 If you ever need a tool to extract and back up your drivers easily and quickly, this software can do the magic. If you ever need a tool to extract and back up your drivers easily and quickly, this software can do the magic.
Driver Magician is an easy-to-use and powerful tool for driver backup and restoration in Windows operation system. It helps you to extract device drivers from your hard disk and back up them to any location you specified.
You will really appreciate how easy this will make your in case of a system crash or something. When you reinstall operation system after system crash, you just select device drivers you want to restore, then it can restore them from driver backup quickly and easily without inserting any driver disk.
The cool thing is all you need is just a system reboot and all your hardware will be back in peak condition.
But that’s not all, it can back up and restore more items such as My Documents folder, Desktop, Registry, Internet Explorer favourite folder, data files of Outlook and Outlook Express.
The latest version, Driver Magician 3.18, which just hit the software market yesterday, March 20th, has these changes:
- Fixed: a bug of memory leak
- Updated: unknown devices database and drivers update database
- Back up drivers of non-present devices
- Some minor tweaks
Still not sure this is for you?
Here is a list of the features you’ll enjoy:
- Back up device drivers of your computer in four modes
- Restore device drivers from backup in one mouse click
- Update device drivers of your PC to improve system performance and stability
- Live Update device identifier database and driver update database
- Detect unknown devices
- Back up more items such as My Documents and Registry
- Restore more items from backup
- Get detailed information of the hardware drivers
- Clone all drivers to an auto-setup package (.EXE), so you can restore drivers without installing Driver Magician
Ready to experience the magic of Driver Magician?
CLICK HERE or visit http://www.drivermagician.com/
Posted in Backup, Developer, Information Management, Main, Security, Shareware, USB, Utilities, Windows | No Comments »
Tuesday, March 20th, 2007
TrueCrypt is an amazing free disk encryption program.
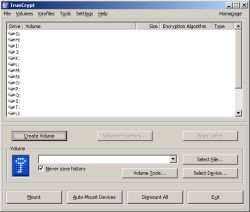 There are a couple of different ways in which you can use TrueCrypt. First, you can encrypt an entire partition on your drive (but not an existing partition). Or, you can create a file on your system that will act as a virtual partition. I like to do the latter because it allows me to backup the partition to DVD or even carry it around with me by putting it on a USB drive, like my iPod. This is handy if you like to carry sensitive information with you wherever you go. There are a couple of different ways in which you can use TrueCrypt. First, you can encrypt an entire partition on your drive (but not an existing partition). Or, you can create a file on your system that will act as a virtual partition. I like to do the latter because it allows me to backup the partition to DVD or even carry it around with me by putting it on a USB drive, like my iPod. This is handy if you like to carry sensitive information with you wherever you go.
The following main features are some of what make TrueCrypt simply the best disk encryption software around:
- TrueCrypt partitions look and work just like any other drive. Once you mount a TrueCrypt volume–by entering the volume’s password–it gets assigned a drive letter. So you can deal with the files just as you would if it were a secondary hard drive (copy, paste, delete, etc.)
- TrueCrypt is both free of charge and it’s open-source; which means you can trust it to do what it claims.
- TrueCrypt doesn’t use the Windows registry. Instead, it uses an XML file. This makes it portable and version compatible. Not only can you use TrueCrypt on XP, 2000, Windows Server 2003 and Vista, but you can use it on Linux and OS X (and it will probably be ported to even more operating systems than that.)
- TrueCrypt volumes can exist on CD’s, DVD’s, USB drives and so on (as long as you make sure to use UDF or FAT32 file systems).
- TrueCrypt affords you plausible deniability. What this means is that if, for whatever reason, some adversary tries to get at your files, they not only wouldn’t be able to hack your encryption. They wouldn’t even know that you encrypted anything in the first place! There’s simply no way to prove you’re using encryption. TrueCrypt makes your encrypted volumes undetectable as being encrypted. Instead, they just look like some random garbage file. Also, TrueCrypt allows for nested encrypted volumes. This means you could throw some junk files in the first layer–then tell someone the password for that–and they would only see that junk and assume you cooperated with them, since you gave them your password. However, the real data that you wanted encrypted would actually be contained within that as a second layer, invisible to the adversary.
Of course, to really convince them, those “junk” files should look like something worthy of being encrypted or they might assume you’re trying to trick them.
- TrueCrypt is superior to Windows XP’s built-in hard drive encryption because it’s open-source, portable across multiple Operating Systems and comes with plausible deniability. XP’s encryption doesn’t have plausible deniability because it uses certificates that anyone can view from the windows directory–which means they can know that you’re hiding something.
- TrueCrypt lets you choose from of the best algorithms in existence and you can even layer multiple algorithms on top of eachother for added security; though doing so is really overkill. Unless you really know what you’re doing, just use the default AES encryption. Furthermore, TrueCrypt doesn’t even know which algorithm you’re using. It tries your password against them all, until one works. This feature is needed for plausible deniability.
There are some other things to note: Currently, when you install TrueCrypt it will come with pretty good documentation in PDF form, so don’t worry about finding documentation online. Also, if you lose your password/key you won’t ever be able to access your TrueCrypt volume(s)! There’s no way you can hack your password back; this is truly strong security. So make sure you don’t lose your password. An additional precaution you can take is to back up the header file that TrueCrypt uses. What this allows you to do is change your password and the original key will still work as the master key.
So, I hope I’ve sold you on this program. Many–if not all–of the top security gurus out there use TrueCrypt. But don’t let its sophistication intimidate you. To the user, TrueCrypt is very easy to set up and use; the program will walk you through it very nicely. It’s extremely stable and is even something you could teach your family to use. In fact, another cool use for TrueCrypt is to create an encrypted volume, store some private files in it, and then share that volume–and its password–with trusted persons only. Such as: family, friends or coworkers.
Posted in Freeware, Linux, Mac Stuff, Main, Open Source, Programming, USB, Utilities, Windows | No Comments »
Monday, March 12th, 2007
 i.Scribe is a fairly compact email program with an easy to use interface and it has some good features. These include a split view of folders and items, signatures, drag and drop, previewing and more. It doesn’t require an install and can be run from a USB memory stick or even a floppy disk if needed. It allows you to manage email accounts, check your mail periodically, preview mail on the server, colour code your messages, and more.i.Scribe can import existing mail from Outlook Express, Netscape, Outlook and Unix MBOX. Additional features include plug-in support, proxy support, ESMTP authentication, message templates, its own built-in Bayesian spam filter, intergrated contact database and calendar and more. i.Scribe is a fairly compact email program with an easy to use interface and it has some good features. These include a split view of folders and items, signatures, drag and drop, previewing and more. It doesn’t require an install and can be run from a USB memory stick or even a floppy disk if needed. It allows you to manage email accounts, check your mail periodically, preview mail on the server, colour code your messages, and more.i.Scribe can import existing mail from Outlook Express, Netscape, Outlook and Unix MBOX. Additional features include plug-in support, proxy support, ESMTP authentication, message templates, its own built-in Bayesian spam filter, intergrated contact database and calendar and more.
A very capable little email program with a ton of features, excellent as an alternative to the big guys, or as mobile solution on a USB drive. Check it out.
Posted in Backup, Business, Commercial, Developer, E-mail, Freeware, Information Management, Internet, Linux, Main, USB, Windows | No Comments »
Tuesday, February 27th, 2007
 TrayIt! is a nifty tool for Windows 95/98/Me, NT/2000/XP. It lets you save Taskbar space for minimized windows by creating a small icon, for each application you apply to it, in the System Tray (The System Tray is the area is located near the Windows Clock). TrayIt! is a nifty tool for Windows 95/98/Me, NT/2000/XP. It lets you save Taskbar space for minimized windows by creating a small icon, for each application you apply to it, in the System Tray (The System Tray is the area is located near the Windows Clock).
All you need to do is start trayit1.exe, which becomes an invisible process on your machine, and then press and hold the Ctrl button on your keyboard whenever you minimize an application window. Instead of minimizing the application to your Taskbar, showing a rectangle with the application’s icon and title bar description, you’ll just see the application’s icon in the System Tray. You can then maximize the window by clicking the icon.
TrayIt’s Web site says: “this is particularly useful for background tasks you typically keep running on your PC all day long like your favorite E-mail client, Real Player, etc..” But, for myself anyway, I have a more important use for this tool: What I do is load Trayit! onto my USB drive that I take everywhere with me for use as an external hard drive. I plug this USB drive into computers that aren’t mine, such as my sister’s family room computer whenever I’m over at her place. Then I launch Trayit! from my USB drive which runs invisibly on her computer until the computer is reboot. Every time I run an application that I don’t want closed by another family member using the computer when I’m away, I minimize it with Trayit! before I leave. Now my young nieces won’t close any windows I have open that are perhaps performing a long download, system scan, or whatever, while I’m away. Very handy.
One issue I’ve come across is that some applications, such as mIRC, already implement a special feature when you hold the Ctrl key while minimizing the window (doing so in mIRC allows you to set a temporary password). This shouldn’t be a problem, as Trayit! should still minimize the application properly after your particular application runs it’s special feature.
Posted in Developer, Main, Task Manager, USB, Utilities, Windows | 1 Comment »
|
|
|
 Chances are, you have at least a couple of USB devices connected to your computer at times. It’s a given nowadays to have flash drives, portable hard discs, printers,MP3 players, and other devices regularly connecting through USB ports; So chances are,you’ve likely got rather a few by now. Would you like to know how many, and be able to keep track of what they’re doing?
Chances are, you have at least a couple of USB devices connected to your computer at times. It’s a given nowadays to have flash drives, portable hard discs, printers,MP3 players, and other devices regularly connecting through USB ports; So chances are,you’ve likely got rather a few by now. Would you like to know how many, and be able to keep track of what they’re doing?
 IdentityPal Lost & Found is a free service to help reunite lost USB pen drives with their owners.
IdentityPal Lost & Found is a free service to help reunite lost USB pen drives with their owners. If you ever need a tool to extract and back up your drivers easily and quickly, this software can do the magic.
If you ever need a tool to extract and back up your drivers easily and quickly, this software can do the magic.
 i.Scribe is a fairly compact email program with an easy to use interface and it has some good features. These include a split view of folders and items, signatures, drag and drop, previewing and more. It doesn’t require an install and can be run from a USB memory stick or even a floppy disk if needed. It allows you to manage email accounts, check your mail periodically, preview mail on the server, colour code your messages, and more.i.Scribe can import existing mail from Outlook Express, Netscape, Outlook and Unix MBOX. Additional features include plug-in support, proxy support, ESMTP authentication, message templates, its own built-in Bayesian spam filter, intergrated contact database and calendar and more.
i.Scribe is a fairly compact email program with an easy to use interface and it has some good features. These include a split view of folders and items, signatures, drag and drop, previewing and more. It doesn’t require an install and can be run from a USB memory stick or even a floppy disk if needed. It allows you to manage email accounts, check your mail periodically, preview mail on the server, colour code your messages, and more.i.Scribe can import existing mail from Outlook Express, Netscape, Outlook and Unix MBOX. Additional features include plug-in support, proxy support, ESMTP authentication, message templates, its own built-in Bayesian spam filter, intergrated contact database and calendar and more. TrayIt!
TrayIt!